Compliance: Overview |
2024-04-19 |
Premium Feature — Available in the Enterprise Edition of LabKey Server. Learn more or contact LabKey.
This topic describes how the compliance module supports compliance with regulations like HIPAA, FISMA, and others. Account management, requiring users to sign the appropriate terms of use, preventing unauthorized access to protected patient information, and logging that lets auditors determine which users have accessed which data are all part of a compliant implementation.
Related Topics:
- Compliance: Settings - Control behavior of:
- User account expiration options
- Audit logging failure notifications
- Login parameters, like number of attempts allowed
- Obscuring data after session timeout
- Project locking and review workflow
User Login and Terms of Use
When a user signs into a folder where the relevant Compliance features have been activated, they must first declare information about the activity or role they will be performing.- A Role must be provided.
- An IRB (Institutional Review Board) number must be provided for many roles.
- Users declare the PHI level of access they require for the current task. The declared PHI level affects the data tables and columns that will be shown to the user upon a successful login.
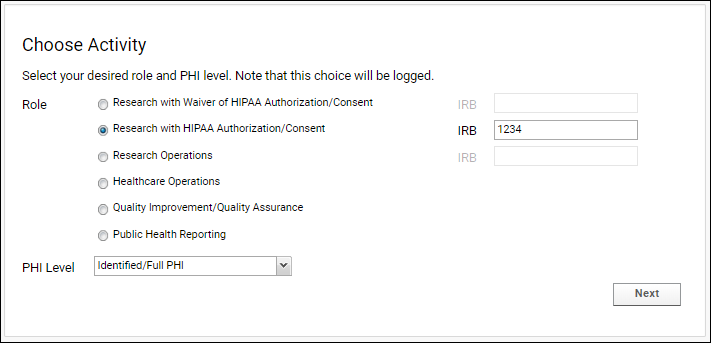 The declarations made above (Role, IRB, and PHI level) determine how a customized Terms of Use document will be dynamically constructed for display to the user. The user must agree to the terms of use before proceeding.
The declarations made above (Role, IRB, and PHI level) determine how a customized Terms of Use document will be dynamically constructed for display to the user. The user must agree to the terms of use before proceeding. Learn more in this topic: Compliance: Settings
Learn more in this topic: Compliance: Settings
PHI Data Access
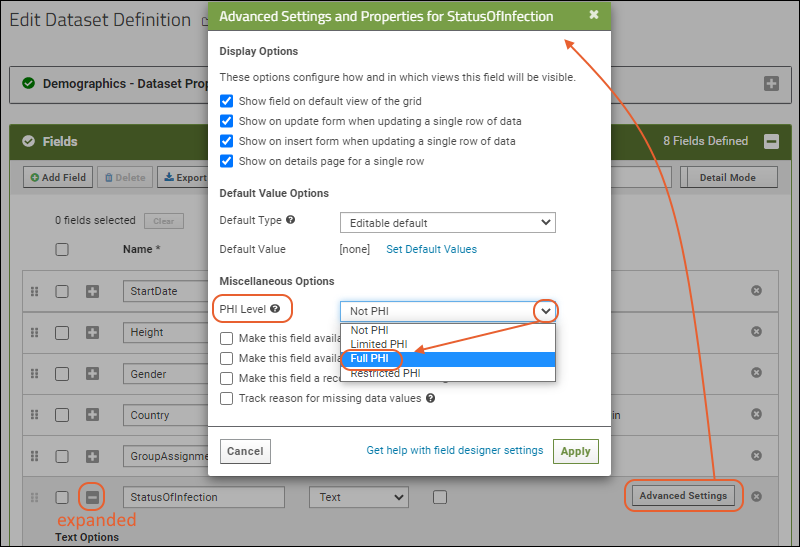
The compliance module lets you annotate each column (for Lists and Datasets) with a PHI level. Possible PHI levels include:- Not PHI - This column is visible for all PHI level declarations.
- Limited PHI - Visible for users declaring Limited PHI and above.
- Full PHI - Visible for user declaring Full PHI.
- Restricted - Visible for users who have been assigned the Restricted PHI role. Note that no declaration made during login allows users to see Restricted columns.
 The Query Browser is also sensitive to the user's PHI access level. If the user has selected non-PHI access, the patient tables are shown, but the PHI columns will be hidden or shown with the data blanked out. For instance, if a user selects "Coded/No PHI" during sign on, the user will still be able to access patient data tables, but will never see data in the columns marked at any PHI level.
The Query Browser is also sensitive to the user's PHI access level. If the user has selected non-PHI access, the patient tables are shown, but the PHI columns will be hidden or shown with the data blanked out. For instance, if a user selects "Coded/No PHI" during sign on, the user will still be able to access patient data tables, but will never see data in the columns marked at any PHI level.
Search and API
Search results follow the same pattern as accessing data grids. Search results will be tailored to the users PHI-role and declared activity. Similarly, for the standard LabKey API (e.g., selectRows(), executeSql()).Grid View Sharing
When saving a custom grid, you have the option to share it with a target group or user. If any target user does not have access to PHI data in a shared grid/filter, they will be denied access to the entire grid. Grid and filter sharing events are logged.Export
Export actions respect the same PHI rules as viewing data grids. If you aren't allowed to view the column, you cannot export it in any format.Audit Logging
The role, the IRB number, the PHI level, and the terms of use agreed to are be logged for auditing purposes. Compliance logging is designed to answer questions such as:- Which users have seen a given patient's data? What data was viewed by each user?
- Which patients have been seen by a particular user? What data was viewed for each patient?
- Which roles and PHI levels were declared by each user? Were those declarations appropriate to their job roles & assigned responsibilities?
- Was the data accessed by the user consistent with the user's declarations?
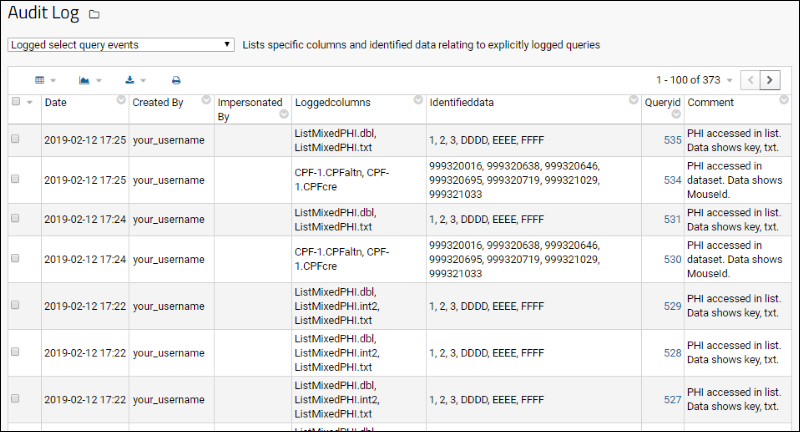
Note that PIVOT and aggregation queries cannot be used with the compliance module's logging of all query access including PHI. For details see Compliance: Logging.